Today, business takes place—often wholly-in the digital realm. With this seismic shift to ecommerce and the need for fast, reliable digital identity verification, fraudsters have learned to game the system with sophisticated schemes designed to siphon money from unsuspecting companies.
International Revenue Share Fraud (IRSF)-an attack where fraudsters hi-jack routine business processes to divert funds in small amounts to themselves, is not new-but it has gone mostly unnoticed for nearly two decades.
As IRSF increases, many businesses have no real solutions to combat it-or even detect it. In fact, with IRSF, bad actors use a company’s own security tactics to defraud them, turning multifactor authentication into a highly lucrative method to skim money, often undetected until the damage is done.
This article provides a comprehensive guide to recognizing and preventing IRSF.
Table of Contents
What is IRSF?
IRSF is a financially-driven attack that artificially inflates traffic by generating calls to number ranges without paying for the calls. The bad actors take a small portion of the revenue made from termination charges received by the number range holder for the inbound traffic.

IRSF attacks target companies that generate a high volume of calls and text messages to their customers, such as call centers or sites that use SMS one-time passwords (OTP) as part of their sign-up process.
Despite being lesser-known than other digital fraud, IRSF is just as costly and growing each year, having grown 6x since 2013 and multiplied total losses from $1.8 billion USD to $10.76 billion USD.

Here’s how an IRSF attack happens, from start to finish:
1. Fraudster illegally acquires premium rate numbers or number ranges to register on app/websites, triggering voice calls and/or messages.
2. Fraudster initiates automated scripts to cycle between numbers in their range. They often test the scripts with a few transactions to see if the number is terminated and then build up or burst traffic to those ranges.
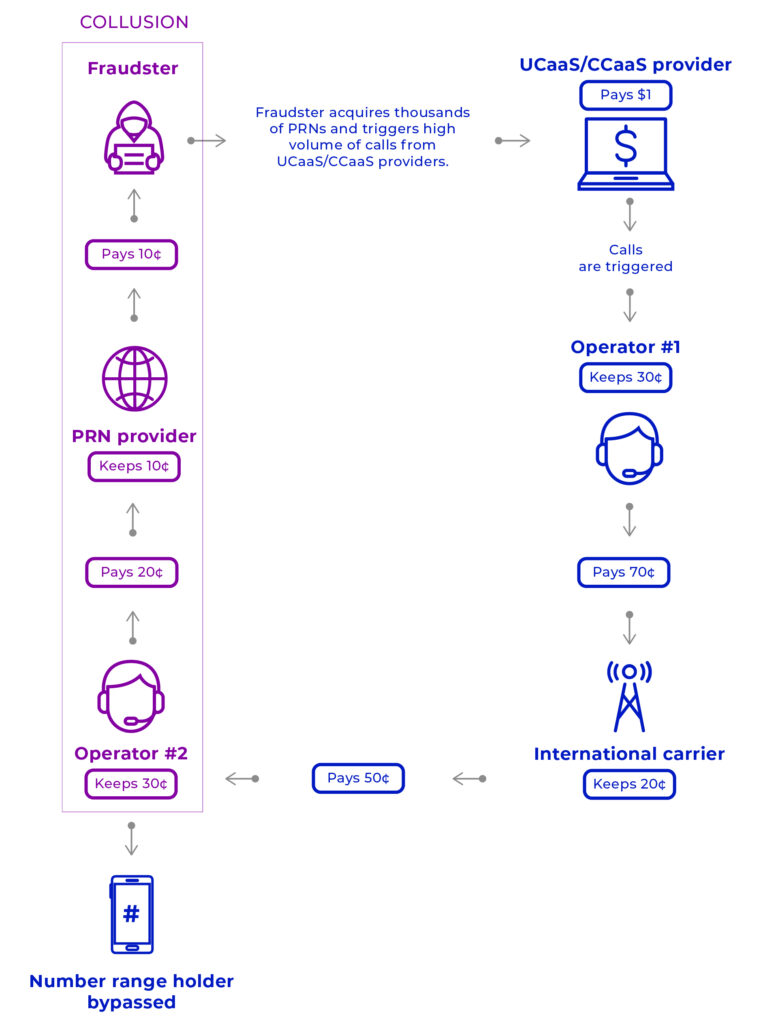
3. Fraudster colludes with IPRN providers and content providers to carry out artificial inflation of traffic from acquired numbers.
4. Fraudster continues to move on to another number of another destination to carry on the traffic until the number ranges are blocked by the originating home operator.
Methods of attack
The following are the most common types of attacks used in IRSF.
2FA onboarding
As most apps and websites are now communication-enabled, companies send SMS messages and voice calls as part of their onboarding workflow or other business processes.
Fraudsters collect thousands of phone numbers to register with these websites, either through onboarding when they receive a six-digit pin through the 2FA process or through marketing messages.
They then drive SMS messages and phone traffic to their own numbers and share the resulting revenue with shady phone carriers. This intricate tactic uses the onboarding process to perpetrate revenue-skimming, often for hundreds of thousands of dollars.
SMS/Voice spam
SMS spam occurs when junk messages are sent to a mobile phone via text. Voice spam is any type of unauthorized phone call made to a phone number.

Callback spam
Lastly, callback spam occurs when missed calls are placed to users from premium phone numbers, in hopes the user will call back incurring an automated charge.
Now let’s examine how these attacks are used to conduct IRSF.
The IRSF process
The IRSF sequence begins when a fraudster illegally obtains premium rate numbers (PRN) or number ranges to register on apps and websites, triggering voice calls and/or SMS messages. SMS IRSF can be to regular mobile or VOIP numbers as well. They then use automated scripts to cycle back and forth through numbers in their range.
Usually, this is prefaced with a test on their scripts, completing some transactions to see if they’re terminated, and then building up or bursting traffic to those ranges.
Next, the bad actor colludes with international PRN providers (IPRN) and content providers to artificially inflate traffic from the numbers they’ve obtained.
Finally, the fraudsters move to a different number (roaming) or destination to carry on the traffic until the number ranges are blocked by the originating home operator.
Now that we know how the process works, let’s look at who is targeted for IRSF.
Who’s vulnerable?
It’s important to understand if you are vulnerable to IRSF attacks, as victims are often unaware that an attack is occurring until the scheme is complete.

Unlike other online fraud, such as ATO or SIM swapping, IRSF targets businesses, not individual consumers. To prevent your business from becoming a victim of IRSF-or to discover if you are already losing revenue to IRSF perpetrators-familiarize yourself with the following characteristics of vulnerable companies:
- Global enterprises with a high volume of daily calls and messages are the number one target for IRSF fraudsters, where they steal small pieces from millions of transactions to stealthily acquire a huge payoff.
- Companies that engage with customers for SMS/voice verification, account openings, and transaction initiation are also vulnerable to IRSF, as fraudsters hijack the verification process to divert funds to themselves.
- Mobile app providers who onboard high volumes of customers quickly while verifying they’re legitimate users are also victims of IRSF. These providers require customers to register through a mobile app downloaded to their smartphones. The new account is verified with an OTP, sent via SMS. IRSF attacks occur by diverting the OTP request to a PRN number that generates high charges.
Detection tips
There are some telltale signs that indicate IRSF is underway.
*Note: These warning signs don’t always signify IRSF, as any one of them could be innocuous or part of another type of attack. However, these are the most common indicators to be aware of in your proactive fraud prevention process.
The first sign of IRSF is a spike in text attempt volume. These attempts often take place across geographical regions.
The location/geography of the incoming communications traffic should also be considered if the particular country doesn’t align with the expected business level of that region.
Another sign to be aware of is the speed and rate at which SMS are incoming. If the messages are received at an unusually high speed, especially if there is a jump from a low to high rate in a short period of time, an IRSF attack may be underway.
Now let’s see how to defend against this harmful attack.
Defense against IRSF
Once you understand the complexities of IRSF and how to detect it, you can start disrupting and eradicating it. Below are the best ways to combat IRSF.
Monitor flagged phone numbers
Monitoring your systems for flagged phone numbers is an effective defense against IRSF, if your system is set up to deliver instant, automated notifications whenever a suspicious call comes in. Before this can happen, however, you need a process that reveals which numbers should be flagged.
Fortunately, there are solutions designed to provide insight into the levels of risk associated with certain phone numbers. These tools automate the process of flagging and monitoring suspicious phone numbers for you.
Note geographic red flags
A phone number shouldn’t raise suspicion based only on its location. However, when all the pieces of information are compiled and viewed holistically, a geographic attribute can help determine if the calls are legitimate or part of an IRSF attempt.
For example, if a call comes from a number associated with a high-risk geographic area, it should then be examined for other factors, such as any recent changes to the owner of the number or differences in location within short periods of time. This way, you can focus on the potential risky number rather than excluding every number from a certain region of the world (which could negatively impact legitimate users and your company’s reputation).
Monitor new traffic patterns
A change in traffic is normal and can be a positive indication of a growing customer base. However, any abnormalities in traffic that go beyond typical fluctuations should be monitored to ensure an IRSF is not in progress. Consider ways to both monitor new traffic patterns and compare them to historical data to provide a baseline for your platform’s traffic.
Implement up-to-date spam blockers
Spam blockers are an effective method to minimize the risk of IRSF. However, companies often allow too many risky users to enter their ecosystem to limit friction for all customers. The key to avoiding this is to use a comprehensive fraud prevention solution that is tailored to your ecosystem and provides legitimate customers quick entry and additional factoring for risky users.
Use caller ID
Caller ID technology has evolved significantly since the days when phone calls were conducted over landlines. Today, companies expect more from the ID systems they put into place. As such, if you install a caller ID to identify callers before answering, you can expect faster automation and more accurate data.
Restrict system access during off hours
Many fraudsters adhere to a predictable schedule when they commit their attacks. Bad actors usually inflate traffic during early mornings and weekends, outside of typical work hours. Since 90% of fraud happens on weekends and holidays, many companies have found success by restricting all system access and outbound calling during these times.
How Telesign combats IRSF
As we’ve seen, IRSF attempts are sophisticated and costly. Fortunately, Telesign has studied IRSF since its inception and can supplement your fight against it with proven solutions that are easy to add to your overall security stack. Telesign Intelligence is the best way to shut down IRSF fraud before it starts.
Intelligence helps you defend against IRSF by analyzing phone number behavior. For example, it can alert you to a particular phone number with a history of sending large batches of SMS messages in a short period of time – a red flag for IRSF attacks.
Here’s how it works:
Using advanced machine learning that evaluates global traffic patterns, phone data attributes, and the world’s largest fraud database, Intelligence delivers comprehensive phone number intelligence to protect you against fraud.

Intelligence not only delivers a reputation score, it also recommends an action (‘allow’, ‘block’, ‘flag’) and uses the action taken to help identify risky numbers quickly and accurately in the future.
IRSF is increasing, costly, and often elusive. But it can be identified and stopped with a proactive approach that includes adding the right tailored solutions into your security stack.
If you’re interested in seeing how Telesign can help you stop IRSF, let’s talk.