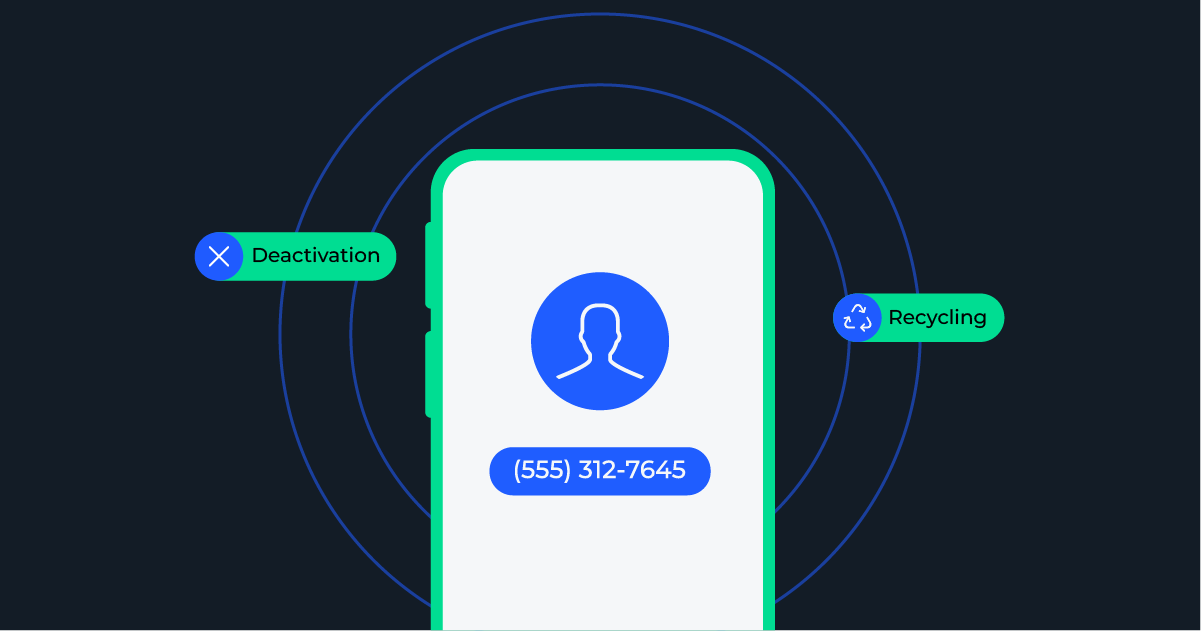
Number deactivation and the recycled phone number dilemma
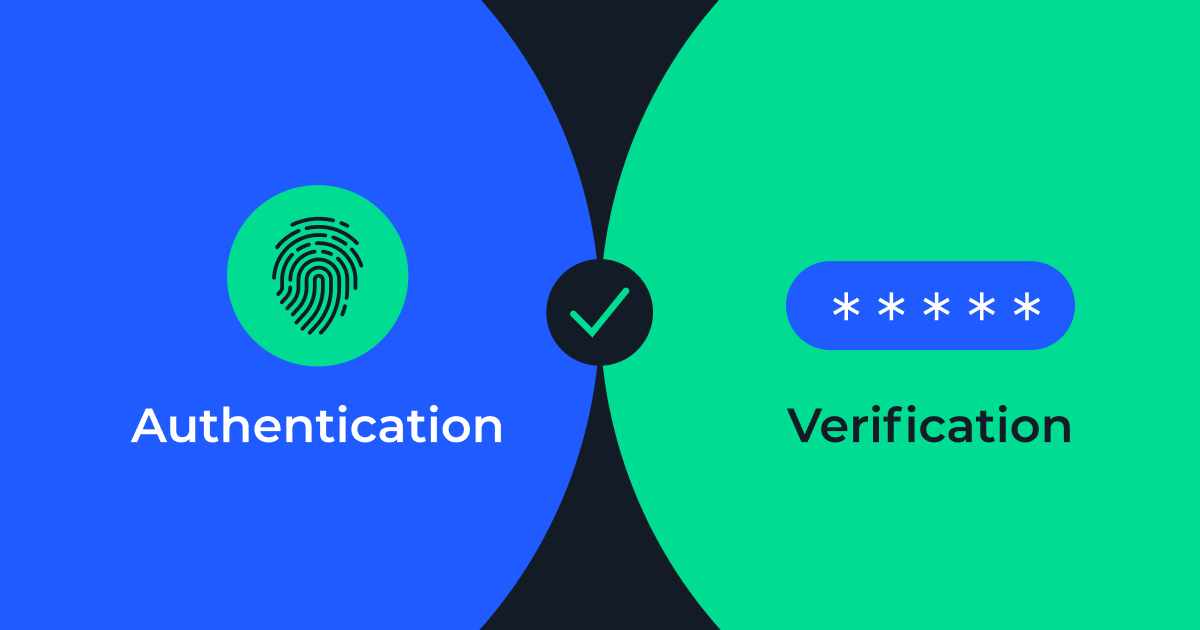
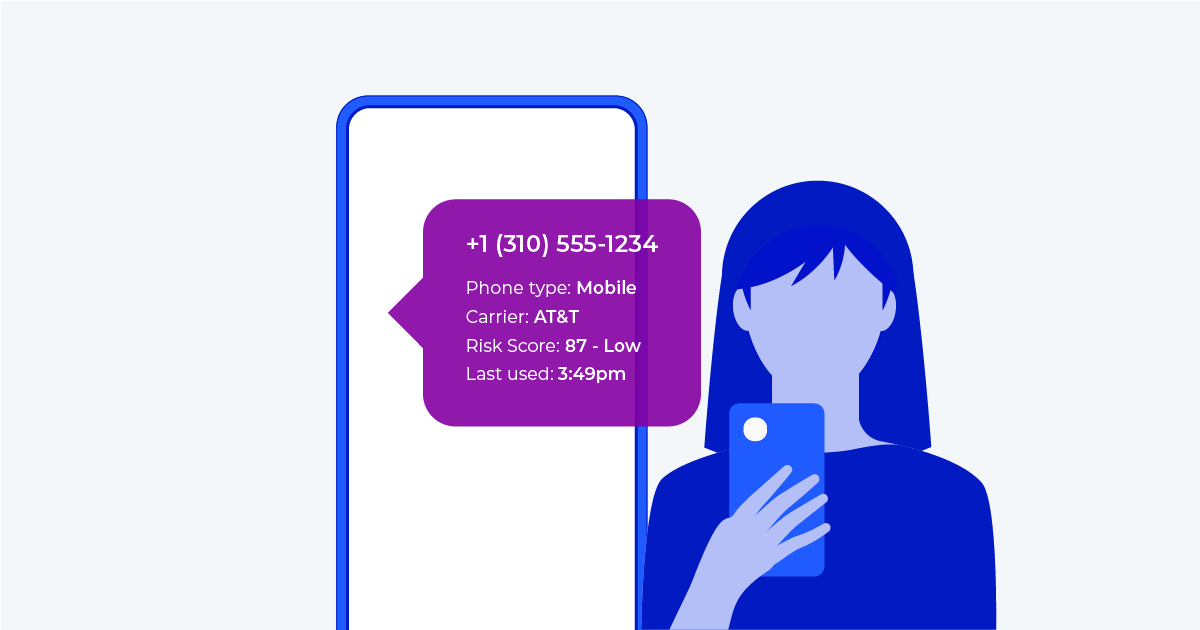
As digital services continue to grow, businesses are increasingly relying on phone-based verification and two-factor authentication (2FA)to safeguard user accounts. These methods are not only user-friendly—they’re also highly effective in confirming a person’s identity through something nearly everyone has: a mobile phone number. With 2FA, a phone number becomes the “second factor,” providing an added